The complete monitoring experience for your phone
Get XNSPY and start tracking calls, texts, multimedia, locations and more on any phone!
Get Started Now Live DemoWith so much of our personal info stored on our iPhones—texts, photos, emails, and even financial details—spyware can be a serious concern. If someone has installed spyware on your iPhone, they could potentially track your location, read your messages, or even access your camera and microphone without you knowing.
Fortunately, knowing how to detect hidden spyware on iPhone and removing them isn’t as complicated as it sounds. In this section, we’ll cover some ways of how to check iPhone for spyware. Plus, we will also guide you through steps about how to remove spyware from iPhone.
Understanding iPhone Security & Potential Security Threat
Apple devices are known to have quite a robust security mechanism. However, the iOS devices and platforms are not entirely immune to cyberattacks. The tech giant is aware of vulnerabilities that hackers use to exploit Apple devices. They do roll out updates to address the issues, but most users are still worried about how easily hackers and cybercriminals can use spyware to steal their information and details.
If you suspect your iPhone’s security and data are compromised, you need to act now.
To help you with this, we have listed all the possible ways of how to check for spyware on iPhones. Also, we will be discussing recommended solutions about how to remove spyware on iPhone.
Before Learning How to Check iPhone for Spyware, Know These Different Types of iPhone Spyware
With over 2.2 billion active Apple iPhones worldwide, it is no wonder that cybercriminals want to exploit the platform’s vulnerabilities. Different types of spying programs affect the iPhone in different ways.
Here are some of what you need to know:
Typical Spyware
Malicious apps or spyware, such as the Pegasus, get installed on your iPhone secretly. Cybercriminals control these apps and remotely view the mobile’s activity.
iCloud Spyware Attack
Hackers access the data synced from the device to your iCloud account. The iCloud attack is possible when a user does not enable two-factor authentication and the hacker accesses their Apple ID login details.
Masque Attacks
Spying tools can be disguised as an update from a reputable app you have installed. However, once on the cellphone, it begins to record activity and steal data.
Hidden Spy Apps
Hidden spy apps on an iPhone give hackers discreet access to device usage and app activity, including messages, emails, calls, locations, media, and social media activity.
Rogue Enterprise Apps
Rogue enterprise apps are usually custom apps mostly developed for particular corporations. The app developers give these apps fancy and cool names, bypassing the App Store’s security. Hackers can use this method to install spying tools and get hold of the phone’s data.
Misusing Pre-Installed Apps
Hackers can temporarily access your phone and use pre-existing apps on the iPhone to access the data. They can even change the logged-in account on the phone’s browser to gather login details and other browsing information.
Zero-Day Exploits
Zero-day exploits are security flaws in software that hackers discover before developers can fix them. These vulnerabilities are called “zero-day” because the developers have had zero days to address the problem. Before you know it, the iPhone can be infected with malware remotely to extract sensitive data.
How to Detect Hidden Spyware on iPhone
Apple devices are revered worldwide for their exceptional security features. However, these devices are not entirely free from spyware applications. Numerous instances have been observed of iPhone users reporting possible hacking. If you suspect the same, the following are the ways on how to check for spyware on iPhone.
i. Look for Unknown or Suspicious Apps
Look for apps on the iPhone that you do not remember installing. The app may not be a default Apple app or downloaded from the App Store. Look out for jailbreak-related apps like Cydia that enable the installation of spyware on the smartphone.
ii. Check for Sudden Data Usage Spikes
Almost all spy programs discreetly run, collect data, and send it to an external server. Notice how much mobile data you use when you perform online activities. If there is a strange and unexplained spike, it is a sign that data is being used by spy software.
iii. Look for Decreased Battery Life
Factors like app usage and battery health impact the iPhone’s battery performance. However, sudden battery drain usually indicates malware or suspicious apps. Spy apps constantly run in the background to collect data, causing the battery to drain rapidly.
iv. Listen for Background Noise on Calls
Spy applications record calls and enable the microphone. If you hear unusual sounds and echoes during a call, someone may be recording it.
v. Observe Slow Performance
Most iPhones are quite fast and can easily perform multiple tasks simultaneously. However, spyware can cause the device to perform even simple tasks quite slowly. Check for spy apps on an iPhone that are causing lags, screen transitions, and buffering.
vi. Watch for Strange Pop-up Ads and Messages
It’s common to receive pop-up ads occasionally. However, getting them incessantly is a sign of spyware, which comes along with adware. This happens when the iPhone is jailbroken or when the app is not downloaded from the App Store.
vii. Identify Random Reboots or Crashes
Due to their constant activity, spy software consumes considerable power. Often, these apps overwhelm the processor and memory, which causes instability and results in sudden crashes and system reboots.
viii. Review Unauthorized Apps or Settings Changes
Most spying tools are installed without consent and modify the mobile’s system settings to avoid detection. You may not notice, but your data and activity are recorded and shared. Therefore, it is necessary to review the phone and app’s settings regularly to prevent potential threats.
ix. Notice Excessive Background Activity
Using the cellphone, you know what apps you frequently use and how much battery or data each roughly consumes. If you notice your device is heating up suddenly, it may be due to spy app activity in the background.
x. Look for Unexpected Text Messages or Calls
Suspicious text messages and calls are one of the telltale signs that a spy program is running on your iPhone. The messages would have strange text and come from unknown senders, while the calls may come at unusual times of the day.
xi. Examine Suspicious App Permissions
Checking for suspicious apps is crucial as these apps often request access to the iPhone’s features and data. Permission for contacts, multimedia, camera, microphone, and messages without any specific need to indicate the presence of spying tools.
xii. Check for an Unresponsive Touch Screen
Malicious apps run continuously and consume the phone’s memory and battery. Excessive use can cause the screen to lag, freeze, and disrupt responsive touch.
How to Remove Spyware From iPhone: 7 Proven Ways
It is difficult to learn how to find hidden spy apps on iPhone since most of them are hidden and run in the background. However, if your suspicions about possible malware are true, you need to be proactive and take measures to remove such spying apps and malware. Here are 7 ways about how to remove spyware on iPhone.
1. Use an Antivirus
The best way to find spyware on iPhone and remove it is by using a top antivirus for iOS devices. This not only makes the iPhone secure but also ensures it functions optimally.
- Download and install the antivirus. Run a scan that will identify and remove the malicious app.

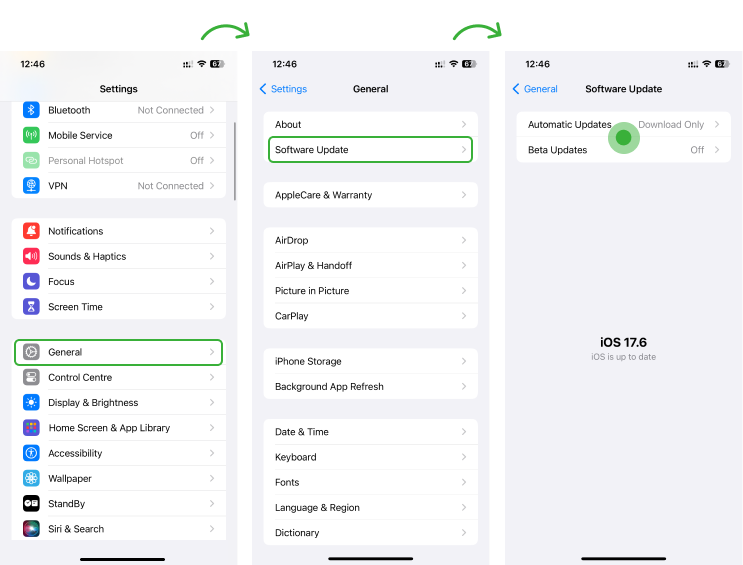
2. Update iPhone to Latest Version
Updating the iPhone to the latest iOS version is quite important. The new update includes fixes and patches for vulnerabilities that spyware can exploit. Keeping the iOS version current means you protect the phone against any malware. Here’s how
- Open the iPhone’s Settings and select General
- Click Software Update
- Download and Install the available Update
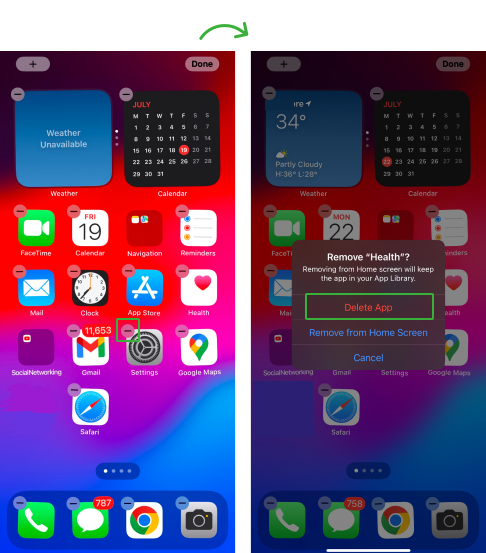
3. Remove Suspicious Apps
Find hidden tracking apps on your iPhone that you do not remember installing. These apps could be recording your activity and compromising your data and privacy.
- Press and Hold the app icon
- Click on ‘Remove App,’ to confirm and the app will be uninstalled.
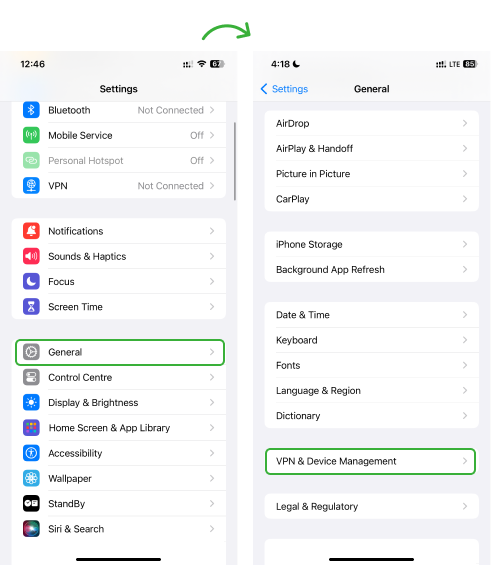
4. Check For and Remove Malicious Profiles
Some spying apps can create new user profiles to grant access to the iPhone’s settings. These profiles also enable the spy tool to log phone usage and other activities. Here is how to check and remove such profiles.
- Open General Settings
- Tap on VPN & Device Management; if you see a profile that you don’t recognize, tap on it and select Remove Profile
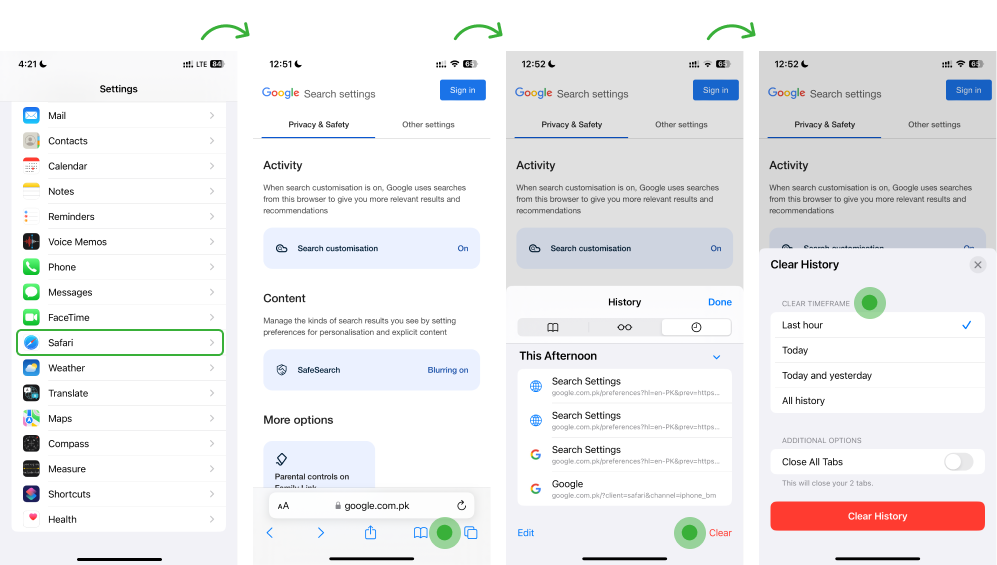
5. Clear Browsing Data and History
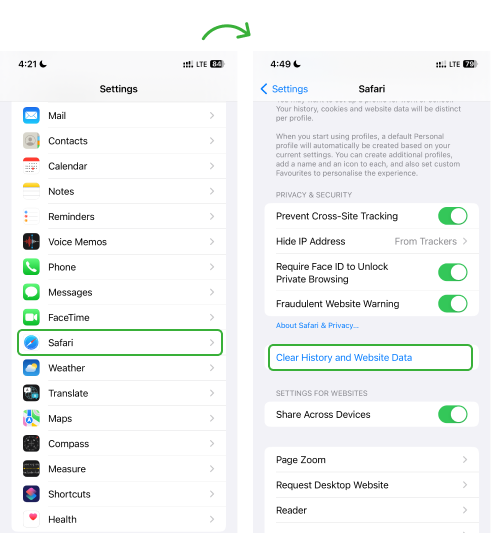
No matter the web browser you use on your iPhone, spyware can infiltrate your browsing data and history. Cookies, cache, and malicious scripts watch your online activity. Therefore, it is necessary to check and clear your browsing history regularly.
- Open Safari App
- Tap on the Open Book icon at the bottom
- Tap the Clear option to delete your browsing history and cookies
- Choose the Time Period you want to clear
6. Factory Reset iPhone
If the steps you took to remove the spy program did not work, the last resort is to reset the iPhone to its factory settings. This step erases the entire contents of the device and restores the phone and software to its original state. However, do back up your data and files as reset erases everything which is very hard to recover.
- Go to iPhone Settings and select General
- Tap the Reset button at the bottom
- Choose the option Erase All Content and Settings
- Enter your Passcode and finish the process by confirming again
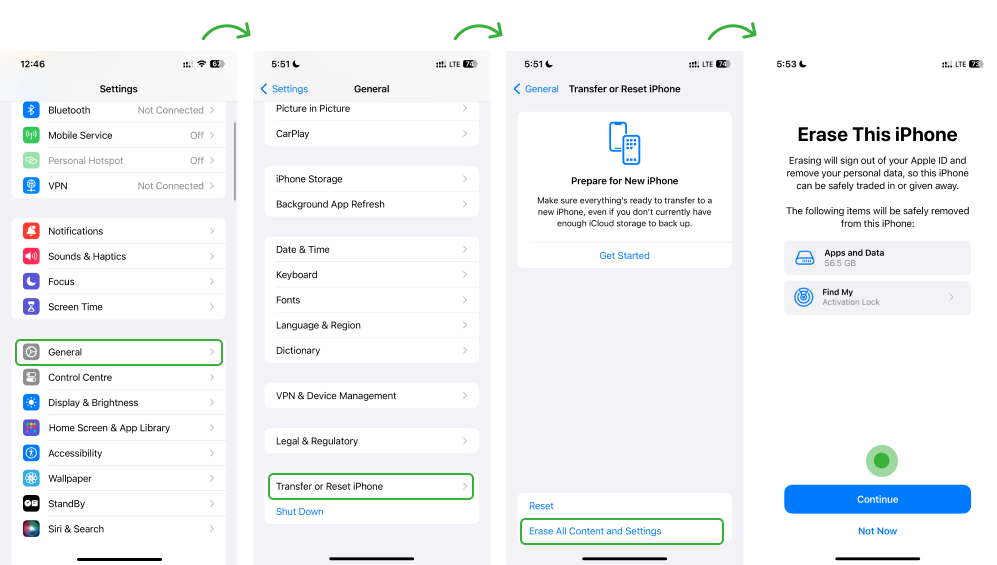
7. Contact Apple Support for Assistance

Apple support is necessary if you run out of options to remove the malware. These experts can guide you through advanced troubleshooting steps. This is done to confirm the presence of spying apps and apply solutions to remove them. Professional support ensures the protection of data and optimal performance of the iPhone.
How to Prevent Future Spyware Infections on an iPhone
While applying the fixes is necessary to completely remove the malware from the device, they do not guarantee the phone’s safety forever. For that, you need to take other important steps to enhance security and protect your data and privacy.
a. Set a Strong Passcode
A strong passcode makes it difficult for hackers to install spyware even if they get physical access to the iPhone. Make a password using numbers, uppercase and lowercase letters, and symbols. It is also recommended that you use Face or Touch ID for identification.
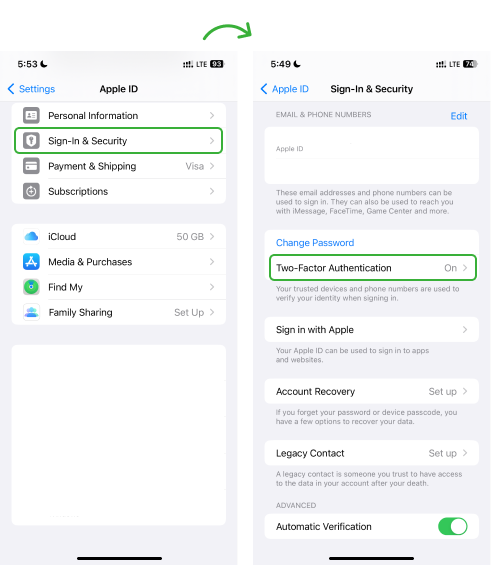
b. Enable Two-Factor Authentication
Hackers can access iCloud and steal data and files synced with the iPhone. You can prevent this by enabling two-factor authentication with your Apple ID. Even if the cybercriminal decodes the password, the 2FA will prevent them from accessing iCloud. You will have to enter the password and a one-time passcode sent through SMS to prove your identification.
Follow the steps below:
- Open Apple ID from the Phone Settings
- Click on Sign-In & Security and tap Two-Way Authentication.
c. Avoid Opening Suspicious Links
You may come across random links often, so avoid clicking on them as they give you direct access to spy software. Clicking the link may even quickly download malware on your iPhone. Do not click on suspicious links you receive in emails, from contacts you don’t know, and while surfing the internet.
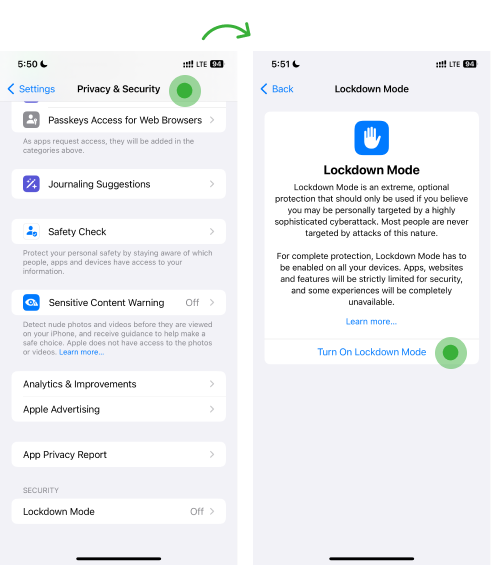
d. Use Lockdown Mode
Enabling lockdown mode is a last-resort step that can be used to prevent inconvenience from robust cyberattacks such as Pegasus. However, this will limit the functionality of the phone’s features, apps, and websites. Also, some apps will not function in lockdown mode.
To enable Lockdown mode:
- Open the Settings app and Tap Privacy & Security.
- Click Lockdown Mode and tap Turn On Lockdown Mode.
e. Do Not Jailbreak your Device
Jailbreaking removes Apple’s built-in security tools and mechanisms and makes the device vulnerable to malware or spyware. Furthermore, jailbreaking also voids the device’s warranty and leads to performance issues.
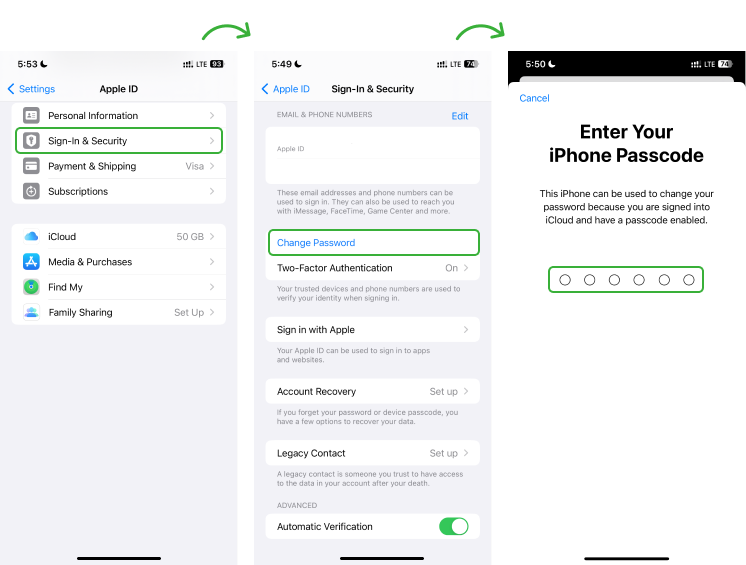
f. Change Your Apple ID Password
Hackers may target your iCloud instead of getting physical access. If you have set a simple password, it can easily be deciphered through the hackers’ advanced methods. You need to set a strong password for your Apple ID. Your email associated with your Apple ID and number will be checked and verified for password reset.
Here is how to change your password:
- Tap Settings and click on Sign-In & Security.
- Tap Change Password.
- Enter the Current Password or Device Passcode, then enter a new password and confirm the new password.
g. Review and Adjust App Permissions
Excessive permissions can allow apps to freely collect personal data, log phone activity, and introduce tools that spy on activity. You need to ensure that the apps only access the required information. Regularly checking and limiting permissions reduces the risk of unauthorized data access.
To Review or change an app’s permission:
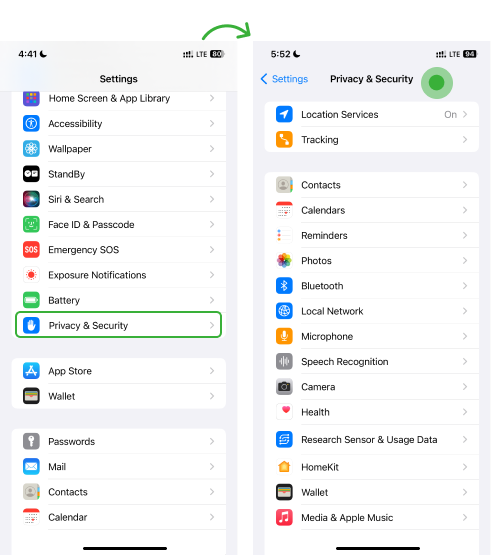
- Go to Settings and Tap on Privacy & Security
- Click Tracking and turn permission on or off for any app on the list.
h. Backup Your Data
Backing up data on iCloud and even copying important ones to your laptop should be standard practice. Not only does it secure your data, but it also helps you erase it if your iPhone is hacked.
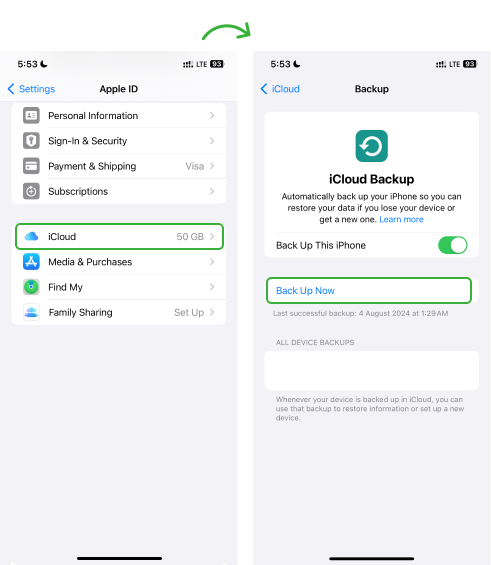
- Connect the device to a Wi-Fi network and go to Apple ID
- Tap iCloud Backup and Click Back Up Now
i. Avoid Downloading Apps from Unofficial Sources
Unofficial and some third-party apps bypass Apple’s security checks. Installing them increases the risk of malware, which can compromise data, privacy, and device performance. Download apps from the App Store, where all the apps are checked and reviewed by Apple.
j. Stay Alert for Phishing Tactics
Today, phishing scams use deceptive emails, messages, and websites to trick you into revealing personal data. This includes fake login pages and urgent information requests. If you receive an email or message from an unknown source, do not open it. Conversely, if you have opened one, do not click on any link or open any attachment.
k. Update Your Wi-Fi Network Password
Hackers easily crack weak passwords, infiltrate the network, and access all connected devices and information. Securing the home Wi-Fi network with a strong password and robust encryption is essential. You must also review the router’s firmware and change the password to avoid unauthorized access.
l. Regularly Clear your Browser History and Cookies
The cookies and cache on the web browsers may contain malicious scripts that can infiltrate the device. Regularly clearing the cookies and cache removes the stored data that could be exploited. For this:
- Open the Browser History
- Tap the Clear option to delete your browsing history and cookies.
5 Comments
Leave a reply:
Your email address will not be published. Required fields are marked*



Renea L. Brand
January 31, 2025 at 7:02 am😱
Aliena
March 24, 2025 at 11:27 amif the spyware is on my iCloud, will factory reset remove it?
Michele R. Wilds
April 21, 2025 at 10:06 amI think my girlfriend has installed something on my phone, I just cannot find it.
Karan James
May 1, 2025 at 2:33 pm😱
Lauren Bissell
May 1, 2025 at 2:37 pmdo i have to pay for antivirus?