How to Hack a Phone: Common Techniques and Methods Hackers Use
Phone hacking is the process of gaining access to a phone without the user's knowledge or consent. With this, hackers can steal your information and access all your accounts, whether social media or banking. When your device is compromised, every aspect of your digital world can be controlled, and every corner of your phone can be accessed.
While hackers can see your screen, in reality, they don’t really need to see anything since they’ll know where everything is. They know where your photos are saved, your passwords are stored, and where all sensitive files are logged.
Hacking into a cell phone involves methods like malware, phishing, or exploiting security flaws. Once hackers have gained access, they can perform widespread actions, including stealing personal data, controlling the device, and compromising user privacy.
Below are the ways that hackers use
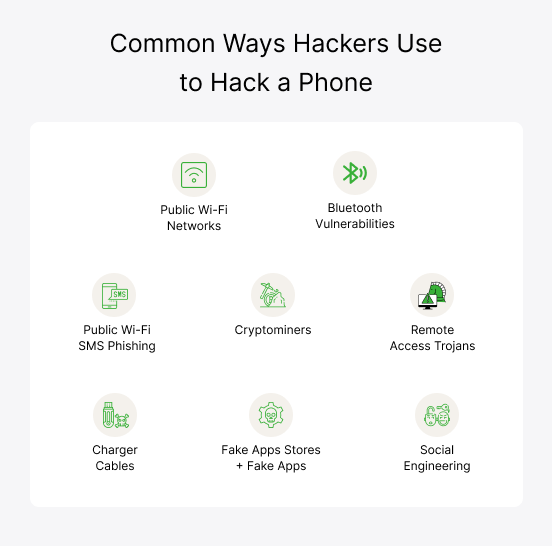
Public Wi-Fi Networks
Public Wi-Fi Networks Users can connect to public networks without any password. However, hackers can exploit these free networks by setting up fake hotspots and using packet sniffing tools. This allows them to spy on phone activity and steal sensitive information like passwords and credit card details. Malware can also be installed on devices to gain unauthorized access and control.
Bluetooth Vulnerabilities (Bluesnarfing)
Bluesnarfing is a cyber-attack where cybercriminals can hack a cellphone through Bluetooth. Hackers exploit weak or unsecured Bluetooth connections to steal sensitive data, such as contacts, messages, and files. Bluesnarfing occurs when the user turns on the Bluetooth and makes it discoverable with any device in range. A hacker can pair it with the phone, which makes this method a discreet and dangerous form of data theft
SMS Phishing
SMS phishing, or "smishing," is a type of cyber activity in which hackers send phony text messages posing to be from trusted organizations. These messages contain links or requests for sensitive information, like passwords and personal details. A user may click on the links and provide information, thinking it's real. However, hackers steal the data, increasing the risk of identity theft and financial loss.
Cryptominers
Cryptomining is used to hack a cell phone by secretly installing cryptocurrency mining software through malicious apps or phishing links. Once installed, the crypto miner uses the phone's processing power to mine digital currencies. This drains the device's resources, causing overheating, battery depletion, and slow performance. The victim often remains unaware, while the hacker profits from the cryptocurrency mined using the compromised device.
Remote Access Trojans
Remote Access Trojans (RATs) are malicious programs that hackers use to get unauthorized access to a victim's phone. These programs enter the device when the victim downloads a malicious game, app, or attachment that seems legitimate. Once installed, RATs operate secretly, allowing hackers to spy on activities, steal sensitive information, and install additional malware.
Social Engineering
Social engineering is a cyber activity in which individuals are tricked into divulging confidential information or granting access to their phones. Hackers pose as trusted contacts or authority figures and use tactics like phishing and pretexting to trick victims into sharing their passwords, PINs, or other sensitive data. Once obtained, the hacker can access the victim's phone to install a hacking app and misuse the data.
Infected USB/Charger Cables
Infected USB or charger cables with malicious software embedded are used to hack phones. When the cable is connected to a phone, it can deploy the spy application and give access to the device. This allows hackers to steal data, track activity, or even take control of the phone remotely. These cables look identical to regular ones and can deceive most users, but this cyberattack is not that common.
Fake Apps Stores + Fake Apps
Fake app stores and fake apps are used to hack phones by misleading users into downloading spyware. These counterfeit platforms and apps mimic legitimate ones and they contain hidden malware. Once installed, the covert program can compromise the phone's security, leading to data breaches or unauthorized device control.
How Will I Know if My Phone is Hacked?
Hackers may look up the latest ways to hack someone’s phone as you try to close off security vulnerabilities with every update.
But they will not be deterred since they still can use multiple methods and sophisticated tools to gain access to your phone, causing unusual behavior and activity on your device. If you want to understand effective ways to counter this, knowing how to hack a phone yourself may help you spot clear signs that your phone has been broken into.
Some signs that you’ve been hacked are:
i. You Can’t Access Your Apple ID or Google Account
You’re unable to access your Apple ID or Google account, which indicates that the phone is hacked. Cybercriminals often change account credentials to lock you out and prevent you from recovering control while exploiting personal data and information.
ii. You’re Unable to Log into Your Online Accounts
Even after multiple efforts, if you are unable to sign in to your online accounts, it is a clear giveaway that the phone is hacked. That is because when devices are compromised, cybercriminals immediately alter passwords to prevent you from accessing the accounts.
iii. You Receive 2FA Codes You Didn't Request
Two-factor authentication (2FA) codes are triggered once a hacker gets access to your login credentials and tries to bypass security. You will receive 2FA codes you didn’t request, which shows that someone has looked up how to hack a cell phone and is trying to get into your accounts.
iv. You Find Strange Photos & Videos in Your Gallery
One telltale sign of unauthorized access to your phone is finding photos and videos in the gallery. Hacking someone's cell phone camera is one of the first things hackers master and use to take control of the camera and capture photos and videos without your knowledge. These multimedia are subsequently saved in the device.
v. You Constantly Have to Quit or Close Specific Apps
Hacking applications installed on the phone can cause certain installed apps to behave erratically and crash suddenly. You’ll notice you must quit those apps that pop up even without constant activity.
Can You Remove a Hacker From Your Phone?
Yes, you can remove a hacker from your phone by using specialized software tools. However, removing them might not be enough. You may not know for how long the phone is hacked and how much personal information and details are exploited. Hackers work quickly once they gain access and gather all the information they seek without you being aware of it.
How Can I Remove Hackers from My Phone?
Now comes the big question – how to remove a hacker from my phone. It is something a lot of people think about, but knowing where to start can make all the difference. But don't worry, these specific steps and solutions can help you remove the hacker and regain control of your phone.
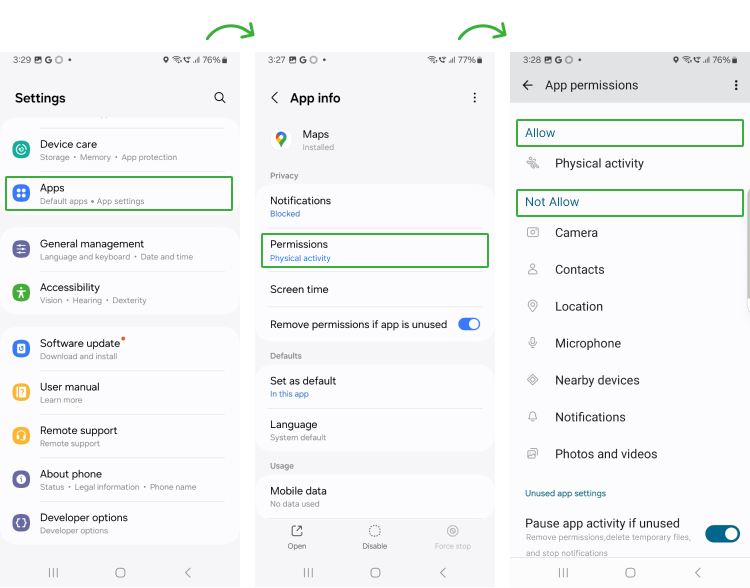
A. Review App Permissions
Reviewing app permissions helps remove hackers by ensuring that apps can only access the necessary data and features. It begins with gaining app permissions to do anything on the device.
By regularly checking and adjusting permissions, you can identify and revoke access granted to suspicious or unnecessary apps. This reduces the risk of unauthorized data access and potential malware exploitation.
To Review app permissions, go into Settings > Apps > Permissions > Allowed/Not Allowed.
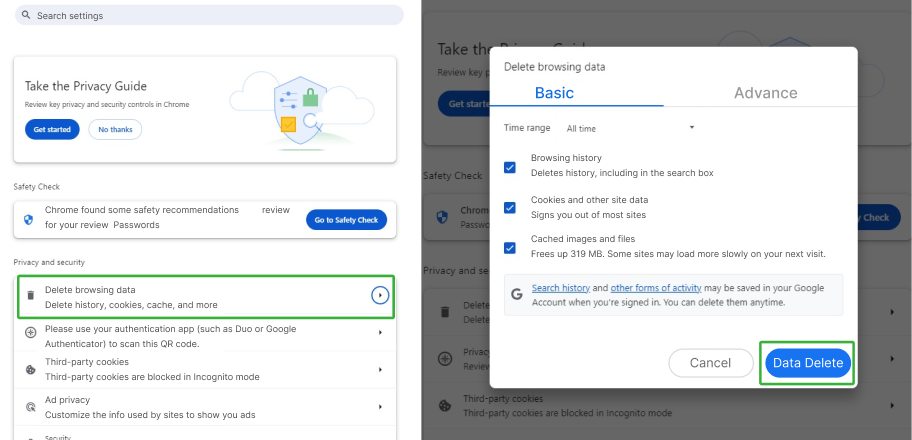
B. Clear Cache
Malicious software can easily infiltrate your phone if you open risky websites or links. Regularly clearing the cache ensures you remove potentially malicious code or scripts that can exploit sensitive information you input on the web browser.
To Clear Cache:
Open Google Settings > Privacy and Security > Delete Browsing History > Delete Data
C. Remove Unfamiliar Apps
Frequently review installed apps to check and remove apps you do not remember downloading. Most likely, these apps are designed to install spyware and hack into someone’s phone to steal data. Removing these apps will reduce the risk of unauthorized access and ensure the phone is secured.
D. Remove Unfamiliar Devices from Bluetooth
Cybercriminals are known to use Bluetooth to pair with devices, intercept data, and exploit vulnerabilities. Hackers can access all the information stored on the phone, from contacts to messages to emails. It is better to disable Bluetooth connection and remove all the connections you do not recognize.
E. Use an Antivirus
Using a popular antivirus removes the hacking threats by detecting, quarantining, and eliminating any spy program from the phone. The advanced antivirus software scans for all types of malware, viruses, and spy apps and provides real-time protection. It is also the most effective way to identify vulnerabilities, block unauthorized access, and remove a hacker from your phone.
F. Remove Jailbreaks/Root
Rooting and jailbreaking are not recommended for any phone as they remove the default security settings on the device. The process voids the warranty of the phone and makes it relatively easy for malicious actors to hack somebody's phone. The data in the phone can then be easily exploited and misused, so it is necessary to restore the phone to its factory settings.
G. Update Your Phone
Digital threat agents tend to identify vulnerabilities in old software versions to install malware. Updating the phone is essential as it includes security patches and bug fixes that prevent the use of any hacking app. Always check the device for updates and install it to secure the phone.
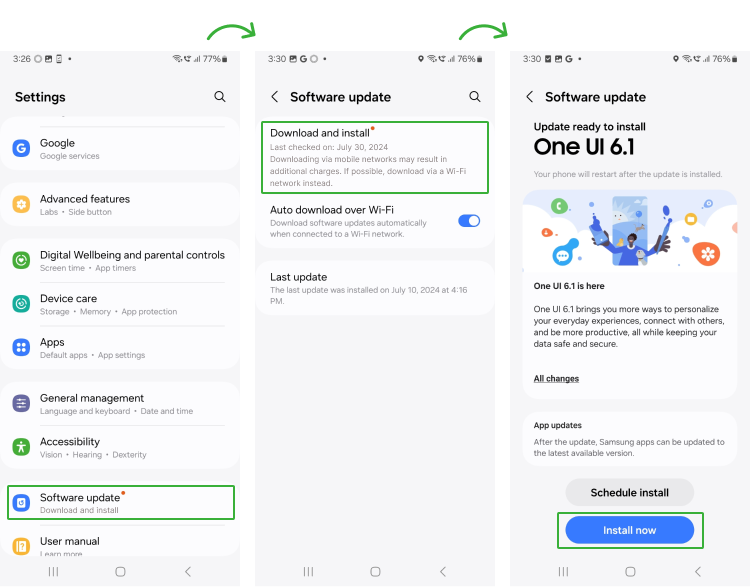
To Check Phone Update:
Click Settings > Software Update > Download and Install > Install Now
H. Delete Suspicious Files
Sometimes, downloading files or applications from unreliable sources installs some suspicious files too. These files may seem unobtrusive but contain malware that can discreetly alter the system configuration, steal data, and track activity. You can use the device’s internal security scan or antivirus to identify and delete these files.
How to Prevent Someone From Hacking Your Phone
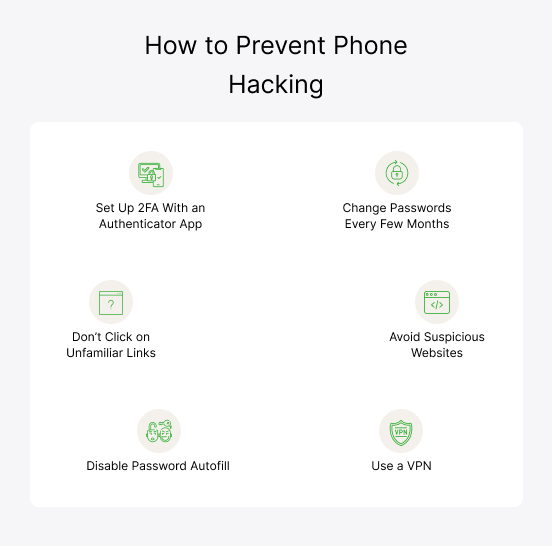
Your device is not entirely immune even if you have removed the hackers once. Hackers can tempt and even be successful in hacking into a phone again. You need to ensure your phone and data remain secure by following the tips below.
I. Change Passwords Every Few Months
Hackers are always looking to exploit weak passwords that have not been changed over time. One of the best ways to minimize the chance of hacking is to regularly change passwords. You also need to set a strong password using a combination of letters, symbols, and numbers. Lastly, you need to avoid using the same passwords for multiple accounts.
II. Set Up 2FA With an Authenticator App
Setting up 2FA with an authenticator app instead of a phone number offers more robust security. This method avoids vulnerabilities like SIM swapping – a technique often used for hacking someone's cell phone number – where hackers hijack the phone number to intercept SMS codes.
An authenticator app generates time-sensitive codes that are stored on the device, making them harder to intercept or replicate. This reduces the risk of unauthorized access to your phone or accounts.
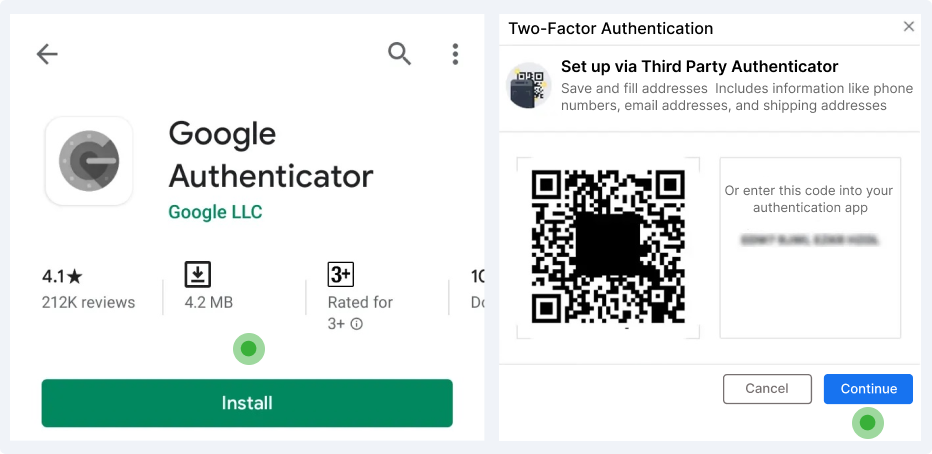
To Set Up:
Download Google Authenticator from PlayStore > Scan QR Code > Continue
III. Don’t Click on Unfamiliar Links
Avoid clicking on unfamiliar links, as mostly these lead to risky phishing websites, malware downloads, and scams. Hackers disguise these malicious links in emails, messages, and ads and trick you into clicking on them.
If you've already fallen victim, learning how to remove a hacker from your phone can help you avoid the damage. Protect your phone and sensitive data from being compromised by resisting the urge to click unreliable links and taking steps to secure your device.
IV. Avoid Suspicious Websites
You can sometimes randomly click and open a website that may seem legitimate but hosts malicious cookies and scripts that can easily infest the phone. Hackers can then access the files and information stored on the device. To minimize risk to your phone and data, you need to steer clear of browsing risky and untrustworthy websites.
V. Use a VPN
Hackers prefer to operate unsecured Wi-Fi networks. A VPN encrypts your internet connection and makes it difficult for hackers to intercept it. It masks your IP address and prevents cyber attackers from tracking your online activities or targeting your device. Using a VPN helps protect your personal information, ensures safer browsing, and reduces the likelihood of hacking.
VI. Disable Password Autofill
Usually, users activate autofill on various apps to avoid entering their details. Autofill even saves sensitive details and passwords you enter, making the device vulnerable if a hacker accesses the device.
If compromised, hackers can easily log into your accounts, alter your passwords, and steal data. Disabling password autofill prevents hackers from unauthorized access to your saved credentials.
Here’s how to Disable AutoFill for Chrome:
Open Chrome Settings > Addresses > Turn off Autofill forms.